Due to the fact that most people don't listen, I've stopped updating this page. If you want to avoid becoming a victim, use the information I've provided on the Internet Help page.
Last updated: March, 2003. Put in the stuff about Deloder. Don't have much time, so I'm keeping it short.
The latest attacks:
March, 2003
Deloder. Also called W32.HLLW.Deloder, Win32.Deloder Worm, WORM_DELODER.A, W32/Deloder.worm, and W32/Deloder-A.
TCP Port 445 attacks: If you're seeing a lot of activity on your firewall or network, you can blame this little guy. Seems to like poking in on TCP port 445.
Only Microsoft operating systems: Thankfully, it only seems to be going after people using Micro$haft's (my special name for Microsoft) operating systems like Windows 2000 and Windows XP. If you're running anything else, you should be safe from it. Linux users should be very happy they're not running Micro$haft products. ;-)
How to avoid getting infected by it: Okay, if you want to make sure you don't get this bad boy, you should remember not to open up attachments that are included with e-mails unless someone said they're going to send you one. This is especially true if the attachment is something like an executable file (.exe), .scr, .vbs, .bat, and so on. Okay, most of us know better, but some don't yet. Hopefully, they'll read this and learn. If you've got file sharing turned on, turn it off if you don't need it. Also anything else along those lines like Web server stuff and all that. If you really have to have those things going, try using better passwords.
Passwords not to use: Don't use regular english words. Using the word password as a password is a very big no-no. If you can find it in a dictionary, or it's the name of someone you know, or the name of a pet, many programs try those first to get access. That's why they call them dictionary attacks. Try using a combination of letters and numbers that's at least eight characters long and something you're sure to remember, but can't be guessed by anyone else, even those who know you and your hobbies. If you can use capital letters and special characters, all the better.
Don't give out your passwords: Some people have been conned out of them by those posing as employees or someone working for the company as a type of network security person. Even heard of some giving their passwords in exchage for a lollypop or a really cheap inkpen. :-P
Anti-virus programs: This is another great way to avoid getting hit by this and other worms and viruses. If you already have one, update the virus defintions. If your anti-virus program isn't kept up to date, it won't recognize something that can screw up your system. Some will update themselves automatically, while others use a live update feature. Still others require you to download the updates and install them manually. Find out what you've got and make sure you do it every few days to a week to keep on top of things.
Firewalls: If you haven't got a firewall yet, get one. Can't afford something elaborate? Grab ZoneAlarm. You can get it free most places like www.download.com. Most of what you'll see on it as hits are on port 80, port 137, port 139 and for now, port 445. There's some odd ones popping in on port 23 and port 443, but there aren't many of them.
January, 2003
W32.Slammer Worm
This is a worm called SQL Slammer by the majority of people, but its more or less official name is the W32.Slammer Worm. Some have called it SQL-Hell, W32.SQLExp.Worm, SQL Slammer Worm, DDOS.SQLP1434.A, SQL Sapphire Worm, W32/SQLSlammer, and MS SQL Slammer. The names really don't matter. It's the same thing.
Internet slowing down: It's why the Internet is slowing down to a crawl.
I noticed something was amiss on the 16th, and did what I could about it. Not sure how far this thing will go, but I got the feeling that if people don't protect themselves, it's going to really spread. What it's doing now is only grabbing territory to establish itself on as many machines as possible. The real attack hasn't really happened yet. Hopefully, people will wise up before it gets bad...
This worm looks for computers running Microsoft's (or as some of us call them, Micro$shaft, but I won't get into that, right now...) Desktop Engine 2000 (MSDE), as well as Microsoft's SQL Server 2000 unless they installed SP3. Once it gets in somewhere, it starts attacking from that new point, kind of like military units conquering territories, then launching attacks from their new bases. The way it attacks is to use randomly generated IP addresses and going to them using UDP port 1434, sending out a 376 to 410 byte sized packet of data, and uses a buffer overflow to get into any of the aforementioned servers it finds. If you look, you might find instances of probes on your firewalls because of this. After the big slowdown, many ISPs and the big backbone carriers engaged filters to block the traffic the worm causes, by blocking UDP port 1434. This isn't a very good idea, because that port's used for name resolution. That's probably one of the reasons why a lot of people are getting not found messages for a lot of the main domain names...
Makes you wonder if the NSA (National Security Agency) is going to retract Microsoft's SQL Server 2000 C2 rating? <weg> Sorry, guys, I just couldn't resist telling about that. ;-)
Didn't really log most of the errors until just recently, but Cnet was one of them. Here's a brief list with pictures to show you some examples:
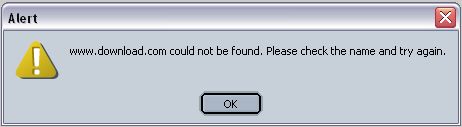
Download.com is one of the main sites to get freeware and shareware, and is owned by Cnet. When this went down, it kind of got everyone's attention.
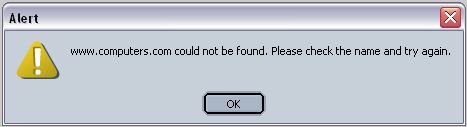
Computers.com, another Cnet owned site went down.
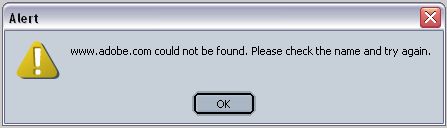
Adobe.com, the makers of Acrobat Reader goes down, as well. Okay, not too crazy about them after Dmitry Sklyarov was arrested for pointing out security flaws in their software on July 16th, 2001, right after DefCon9, but this was another bad sign.
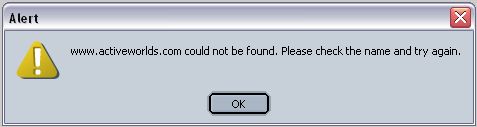
Activeworlds.com, the makers of the 3D chat program starts having problems, too. Because AW seems to be supporting slavery, you can understand that I didn't shed a single tear over their problems, and in fact, I let out a really big joyful how. Note to my neighbors: Sorry about that, it couldn't be helped. ;-)
Cybernetworlds.com also couldn't be reached. Cybernetworlds uses the AW 3D chat program client mentioned above, but for their own universe, Cybernet Worlds. I was once told that they would not allow slavery in their universe, but they seemed to have changed their minds later, and welcomed slavery into their universe with open arms. :-( Seeing that their server was having problems was cause for another long joyful howl. Hee hee hee My neighbors probably think I'm drinking again.
Rut-ro! Radioshack.com was also having problems!
Getting curious, I did a little... 'checking around' and it seemed that even Microsoft's database server was down. Woe to those who are trying to register their copies of Windows XP! Guess if you couldn't register your copy of Windows XP, you know why, now.
What about my site, you ask? I noticed some odd things in the traffic to my site at cyberwolfman.com on the 16th, but things were pretty much set right for the server shortly after. :-) By the 19th, it was business as usual. The humans above are just a little slow at figuring out the score, is all.
Here's proof:
So, you're curious to know if you're infected and you're running Windows? Here's what you do:
Go to the command prompt or MS-DOS prompt or whatever the heck it's called on your system, type in the following, then hit the Enter or Return key:
netstat -an | find "1434"
If you don't see anything listed that's listening on that port, it's a safe bet that you're clean of the worm. To those not in the know, you can find that | character right above the \ on most keyboards.
To those people running Microsoft's Desktop Engine 2000 (MSDE), and Microsoft's SQL Server 2000 who want to protect themselves:
Download the available service packs or patches and install them! Patches for this vulnerability have been available since July of 2002. Stop procrastinating, already! Download what you need, set the server to manual, re-boot the computer that's got the problem, install the service pack or patches, and re-boot to be safe, then put the server back on automatic. Since the worm only exists in RAM, all you have to do to get rid of SQL Slammer on an infected machine is to re-boot after you've installed everything. Cybernetic exorsicm made easy. Let's exorsice those demons out of you! LOL Just don't get demon exorcism with exercising demons. ;-) Great, now I've got this picture of several legions of demons doing calisthenics in a gym with flames all over the place. :-P Of course, it'll probably just get re-infected again unless you install the service pack or patches, so get with it!
Update your anti-virus program by getting the latest definitions!
Repeat as needed and fairly frequently! This way, you won't get caught un-aware in the future!
If you can't do any of the above: Use filters on traffic using TCP and UDP ports 1434 and 1433. (Just in case because SQL uses both.) Don't close the ports! Duh?
Why should you be so worried about this vulnerablity in your system if all it's doing is spreading itself around on the Internet by using your computer? Let me give you the 411 / heads up / datafeed on the situation:
If an attacker can get into your system by using this flaw, they can have system privs and possibly administrator access. Got your attention now? Oh, joy!
Want my advice for the safest way to go with software? Use something else besides Microsoft products if you can't keep up with updates! Because so many people use them even for e-mail, a lot of viruses and worms are created to use their products. Oops!
What I wrote for Cnet about DDoS attacks way back in 2000:
Whereas at this time in history, the DDoS attacks are perceived as the primary danger to the big, bad Internet companies, it's pretty much guaranteed that even if they can secure themselves against this threat, the next one is just around the corner. It's like a type of wargame. One side erects defenses, while the other attacks. For a while, the defending side can secure itself, but in time, the attackers spot a vulnerability within the defensive fortification and then go at it en masse like ants on a pile of spilled sugar or a large group of pre-school children all jumping on a toy car that looks especially tempting because another child finds it fun, and is having a good time playing with it. You don't have to be an atomic physicist to figure out what's gonna happen to the toy car when a large group of screaming kids jump on it all at once. This vulnerable spot could be something as utterly simplistic like poor access control at the gate, or because the defenders didn't plan on the attackers using something totally unimagined by them and find themselves unprepared for such an event. If it was me, I'd be slamming shut the portals where invaders could enter that I didn't really need so fast that they'd cause a sonic boom, and then asking those knowledgeable about such things what I could do to keep myself and my kingdom safe. Perhaps the wise and kindly wizard may have some ideas? ;-)
Yeah, you probably figured it out. They're still not listening to me. Not even Cnet, who had problems, too. Well, they've only themselves to blame. I did try to warn people.
To CyberWoLfman's Web Asylum main page.
Copyright © Cyberwolfman™ aka CyberWoLfman™ aka Grok Wolf. All Rights Reserved.